 Recently my school had an audit of our G Suite for Education domain and one of the findings was for a footer/disclaimer/confidentiality statement to be appended to the emails sent from the school.
Recently my school had an audit of our G Suite for Education domain and one of the findings was for a footer/disclaimer/confidentiality statement to be appended to the emails sent from the school.
For those of you unfamiliar with what this it, it would place a block of text at the end of every email sent by the school (Google) without user intervention and regardless of where it was sent from. Whether it was the Google web interface, a desktop mail client or a mobile device, every email would have the footer appended to it.
It could be applied to any domain/organization unit (OU) within the system. Faculty, staff, administrator or students could be included.
The auditing firm provided examples for the footer text for employees and students:
EMPLOYEES
“This is a staff email account managed by [[SCHOOL]]. This email and any files transmitted with it are confidential and intended solely for the use of the individual or entity to whom they are addressed. If you have received this email in error please notify the sender.”
STUDENTS
“This is a student email account managed by [[SCHOOL]]. The contents of this email are governed by the laws of the state and the board policies of the school district.”
This is something I have seen other school and organizations do but hasn’t been considered or discussion here.
The is also some litigation around whether these clauses protect the confidentiality of these emails, but this wasn’t what interested me or how I was considering the recommendation.
As I thought about the recommendation something struck me… this could help our efforts to fight phishing!
How you ask?
 Well… in one recent example phishing attack that hit many independent schools, we had to deal with the “Headmaster” email.
Well… in one recent example phishing attack that hit many independent schools, we had to deal with the “Headmaster” email.
In the email (see below) a request for an iTunes gift card is sent someone and the “From” address includes the name of the school’s headmaster, however, the email address is incorrect.
This should be a telltale sign, however, it is often overlooked as many people open, responded, and close emails without ever fully looking at the “From” address.
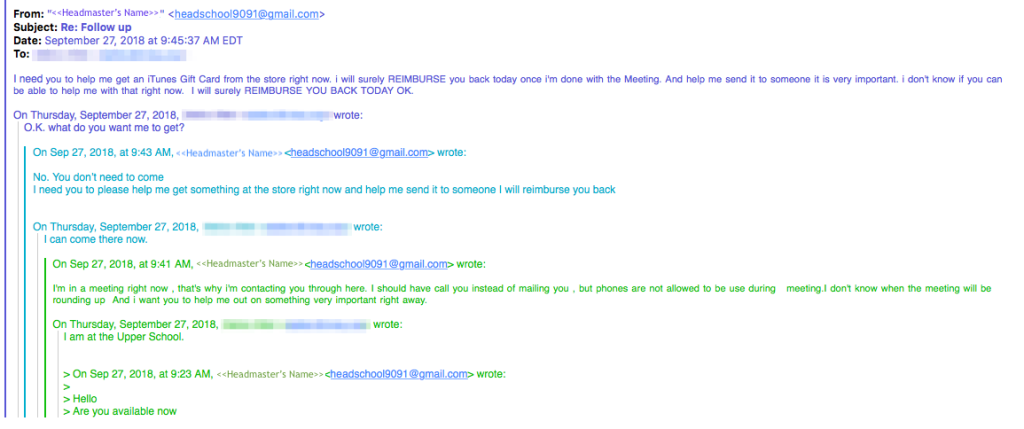
An exchange can go on for a while before the recipient becomes aware of the fact that they are being phished.
If the message sent had something, other than the name of the sender to identify it as a school email it “might” help the recipient know if the message is legitimate or not.
A signature block within the message could help, but often this is something that needs to be configured within whatever tool you are using to send your messages (browser, application, mobile device or tablet). Even with this configured properly it is often up to the end-user as to whether or not to include the signature in the email.
As mentioned at the start, by using a footer applied by the sending email server to EVERY message regardless of the sending device or platform, it would be like applying a watermark to every email.
This could be ONE of the things to look for when sent questionable emails to determine if it is a legitimate message or phishing attempt.
In a spear phishing attempt, a perpetrator may have had some communication with the school in the past to try to identify specific targets and engineer the best possible attack. This would likely include the footer as they would highly focused on something more than an iTunes gift card.
With all of this to consider it is important to conduct ongoing, annual training of employees and students.
We must continue to look at ways to help our user identify risks and make smart choices. Educate our users on the threats they face and giving them the things to look for tools to combat them is something we must do on an ongoing basis.


